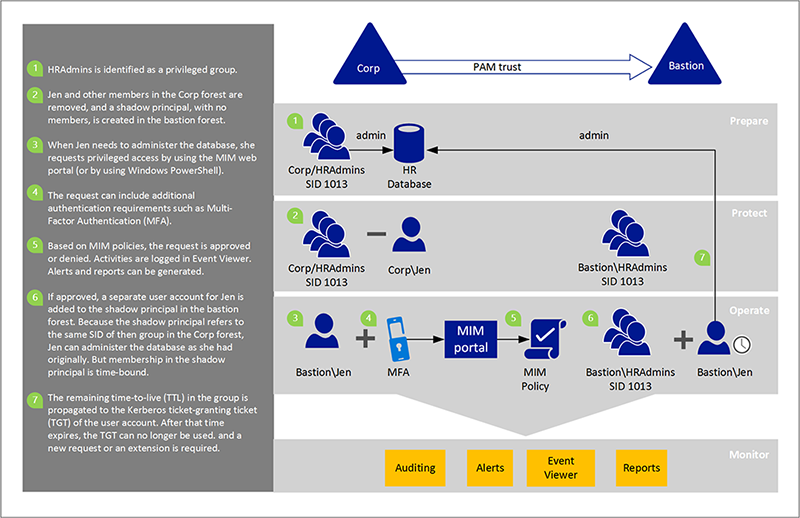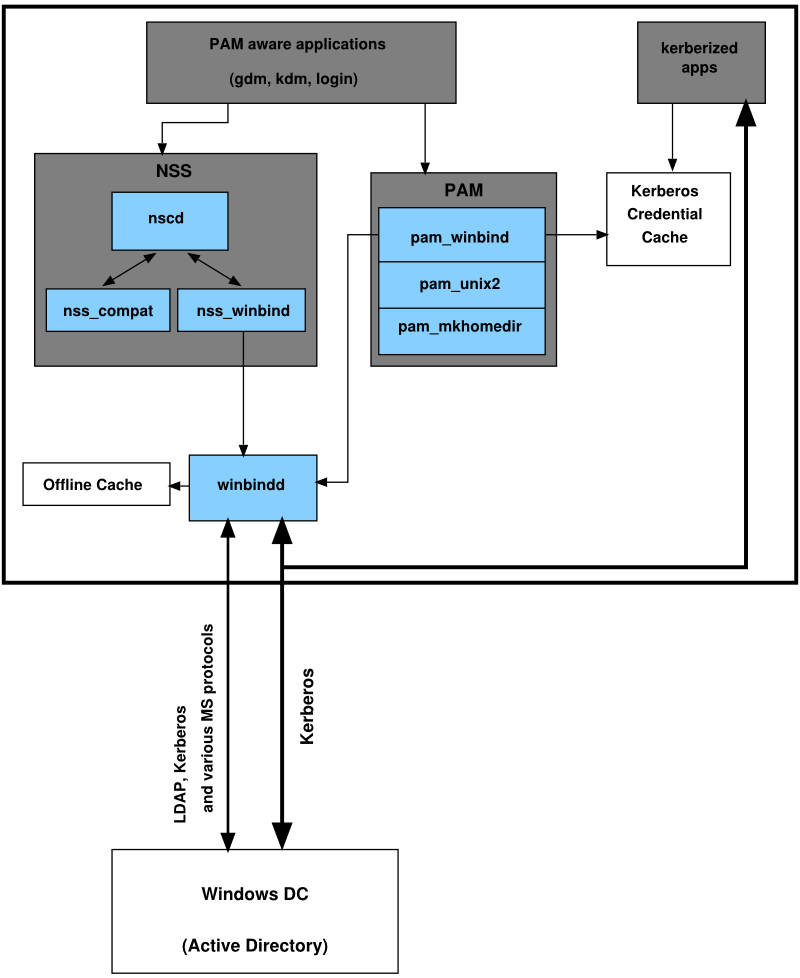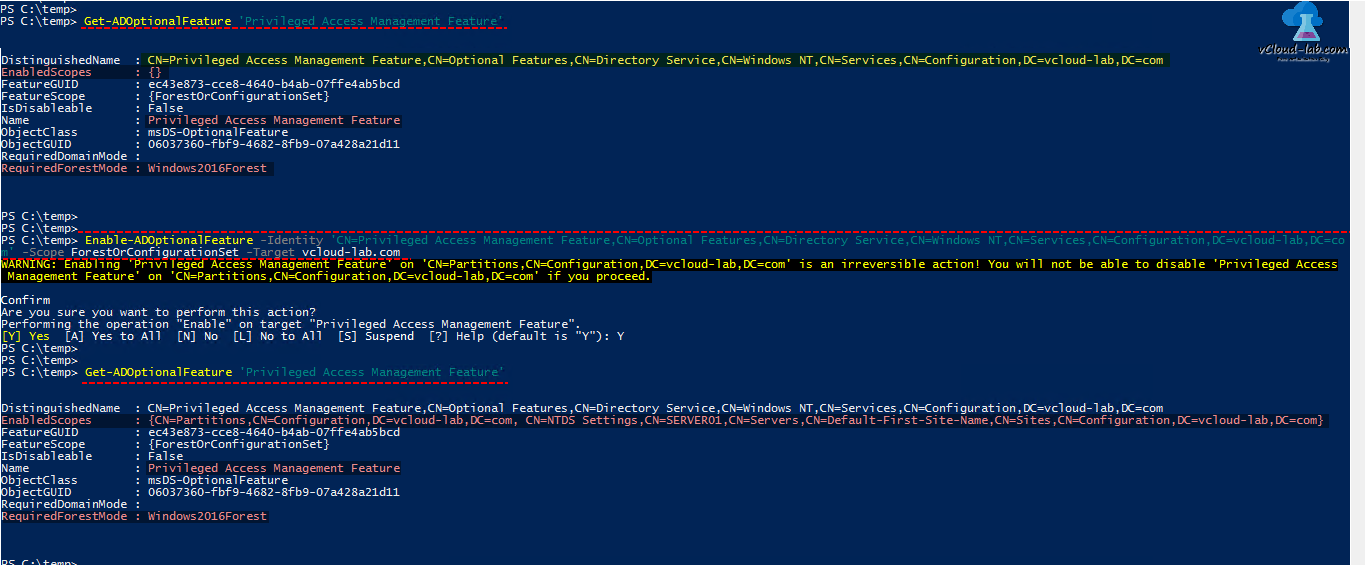
Powershell: Temporary group membership on Windows 2016 Active Directory | vGeek - Tales from real IT system Administration environment

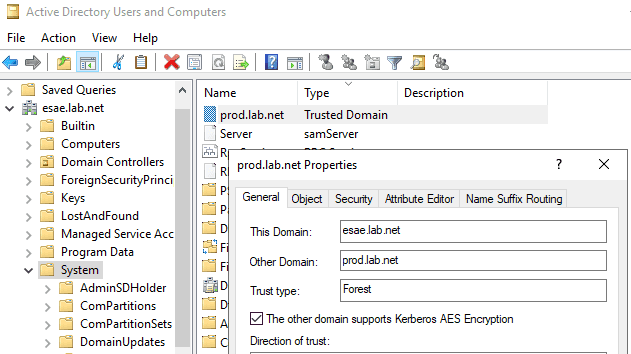
Microsoft Privileged Access Management for Just-in-Time Administration | ITPro Today: IT News, How-Tos, Trends, Case Studies, Career Tips, More
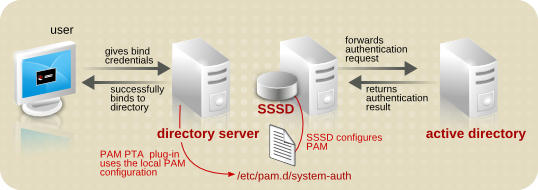
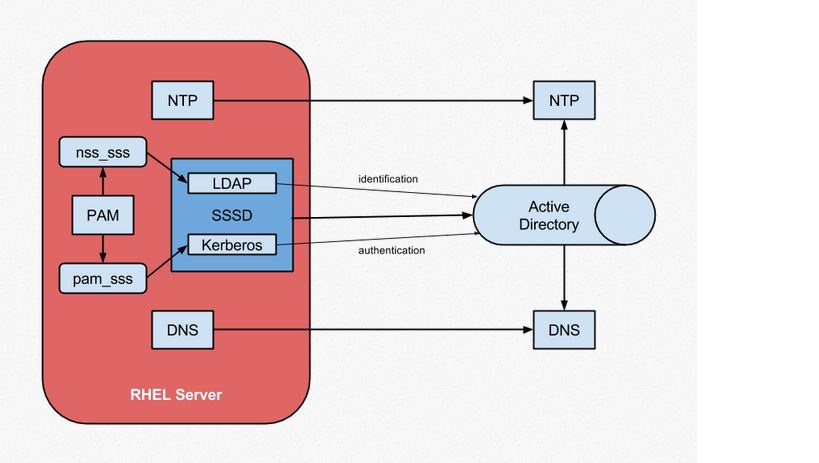
20.15. Using PAM for Pass Through Authentication Red Hat Directory Server 11 | Red Hat Customer Portal